How to secure Xero in your Small Business
Here in Australian Xero has all but taken over the small business accounting space. As a pioneer in cloud accounting, they’ve been leading the way in improving the experience for small business owners for years.
Unless you’re a cloud accounting platform provider yourself, moving to a service like Xero is a fantastic idea. Not only will you get access to the latest and greatest features, you’ll also benefit from the security expertise and focus of the Xero team. That is provided you hold up your end of the cybersecurity bargain.
Lets step through a common security incident involving Xero. Along the way I’ll highlight some of the things you can do to avoid the same thing happening to you.
Someone is sending invoices from your Xero account
“Hey, its been a while. Just calling to confirm the details from this latest invoice you’ve sent through ...”
Its always great to talk with customers and clients, especially awesome ones. But what if they’re calling about an invoice you never sent?
Figuring out where a Xero invoice was sent from?
DKIM and SPF can help verify that email was sent from you. Look to implement it in any system that communicates on behalf of your business.
Proving that an email has come from your business or a specific team member can be tricky. Depending on how you host your email, there are ways you can prove they’re being sent from your account. A lot of cloud apps support sending verified emails from your own domain using something called DKIM and SPF. Unfortunately Xero is not currently one of these.
While you can add your logo and a bit of branding, without support for security features like DKIM or SPF you need to rely on Xero emailing invoices from their domain on your behalf. This isn’t the end of the world, but does mean you’ll probably need anyone receiving a dodgy email to forward you a copy before you can start figuring out where it came from. It’s worthwhile encouraging customers, suppliers and your team to verify in person any changes sent over email, just like your awesome customer has.
Your awesome customer forwards on the email for you to check over, relieved to have a bit of time up their sleeves before needing to pay.
On the surface everything looks legit:
It has the right logo and branding.
It references items you typically invoice for.
It includes your email as the reply address.
The only thing that’s is the account details at the bottom of the invoice. Your awesome customer would have sent money to the wrong account if they hadn’t contacted you first! 🚨
Time to jump on Xero and see what’s going on.
How could someone send an invoice through Xero with the wrong account details?
Multi-factor authentication is a critical security measure you should implement on anything you can access over the Internet
Towards the end of 2018 Xero began to force Australian users to authenticate their accounts with more than just a password. This was based on a requirement from the Australian Tax Office and ensures Australian users of Xero are protected with something called Multi-factor or Two-step authentication. You can check to see if two-step authentication is activated right across your team in the Users area of Organisation settings.
Logging into Xero to see what’s happening you’re prompted to enter the code from your mobile, confirming that the security of your account is still intact. Opening up the Invoices page there it is; the invoice your customer contacted you about. 😰
Having good logs of what’s happening in cloud appl is really handy for figuring out what might have gone wrong.
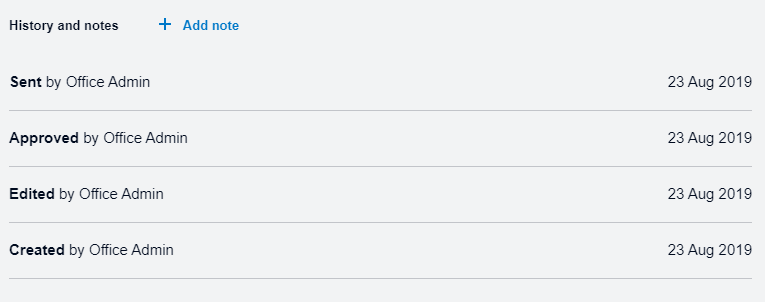
If you take a look at the bottom of the screen when reviewing an invoice you’ll find an option to Show history and notes. Clicking on it will show you all the details of how this invoice was created and when it was sent. Xero surfaces this sort of information throughout their platform to help you understand what’s going on in your business. Knowing where these sorts of details can be found is invaluable when things go wrong.
Looking at the history of an invoice tells you a few things:
The invoice was sent from your Xero organisation.
When it was created and sent.
Which account created, approved and sent the invoice.
You confirm the invoice was indeed sent from your account and it looks as though the Office Admin account is at fault.
But how could someone get into one of your Xero accounts?
There are a few ways this could happen:
Make sure you and your team don’t reuse passwords across multiple systems.
Xero have only been enforcing Two-step authentication for the last year. It may not have been enabled on accounts not used in a while.
Someone might have disabled Two-step authentication and forgotten to re-enable it.
The phone associated with the account could have been taken.
One of your team members with access to the account may be doing the wrong thing.
A 3rd party app from the Xero market place could be doing something inappropriate.
Since you stopped using the Office Admin account years ago, you suspect it was never setup with Two-step authentication. While the password is long and complex, back in the day it you often used the same password for this account whenever signing up for new cloud app.
If you reuse a password across multiple services it’s likely the password will be discovered at some point making it possible to be used to get into Xero. The bigger questions at this point though is, why does would an account like this exist at all and what else might it have be misused for?
How to control access to your Xero organisation?
Separating your subscription account from your personal Xero login is a great idea, but its critical that you take extra care to ensure its secured with a strong password and tightly controlled. By having a separate account for administration, you can configure the other accounts used by your team to have only the access they need to do their jobs. You can control the access your team has from the Users section of the Organisation settings area.
Here are a few things to keep in mind when you’re configuring access:
Limit the number of users with an Admin role. If you have a larger team keep it under 5, ideally it should only be 2.
Aim to assigned the lowest permissions possible. If someone only needs read-only, just give them that.
Don’t give access to features if they’re not necessary. If someone doesn’t need Payroll access, don’t give it to them.
You can limit the chances of something going wrong by making sure your team’s access is restricted to only what’s needed to do their job.
Taking the time to configure access for your team up front also means you’ll know where to go to remove their access if there’s ever a need. Like, for example, their account starts sending dodgy invoices to your awesome customers!
Unsure of what’s going on with the Office Admin account, you reduce its access to read-only to make sure it can’t to any more damage.
Can you find out who’s misusing your Xero account?
Regularly reviewing access logs can help you spot something dodgy happening before real damage is caused.
While Xero give you some good detail in areas like invoice history, the details you need to figure out who’s been using one of your accounts is a bit limited. In the Users area of Organisation Settings the Login History tab will show you when a user has logged in, but the information appears to be limited to just the last 2 weeks. This information is also limited to names and times which might not tell you much unless they’re logging in at strange times (e.g. in the middle of the night).
You’ll find more details about the last 10 logins from your own account towards the top of the Dashboard page, including the IP address you logged in from and the country associated with it.
Reviewing these logs regularly is a great idea and might help you spot something dodgy going on before it turns into something really serious. Think of it in the same way you might reviewing a credit card statement on a regular basis.
Once something has gone wrong, its more important to figure out how far things have gone.
How to respond to a dodgy invoice being sent from your Xero account?
Finding yourself in the middle of a security incident without a clear plan is a terrible feeling. Your mind is racing a million miles an hour and you can feel the pressure of everyone looking to you for answers you simply don’t have. Creating a high-level response plan in place for when things go wrong ahead of time is worth the effort.
Create a plan for things go wrong and include the contact details of anyone you’ll need to call on for support.
An important first step when responding to any security incident is to try and stop the problem from getting any bigger. Removing a suspicious account’s access as noted earlier is a great first step, but you should also let your team know and encourage them to check the security of their own accounts (e.g. look at their 10 latest logins) and flag anything suspect.
Next, you’ll want to try and figure out how big the problem is. In Xero you’ll want to check over things like Payroll account details, Invoices and Invoice templates, Payment providers and Bills paid for changes that might have been made. You won’t be able to be 100% confident nothing else has happened without outside help, but this will at least give you a sense for how bad things are and who you’ll need to contact.
Now will be the time to call in the experts. Xero support will be key to this, but unfortunately they don’t currently provide phone support. They do though offer 24x7 email support via their website. Details like this should be in your response plans so you don’t have to go looking for them in the heat of the moment.
You spend a bit of time searching your Xero account for signs of more dodgy behaviour but don’t find anything other than the invoice your customer contacted you about. It looks as though the Office Admin account was only used the day the invoice was created and sent. To be on the safe side you contact Xero support asking them to check into Office Admin account.
Xero support can take up to 24 hours to get back to you. This will feel like a lifetime. If at this point you find evidence of more invoices being sent or other things having been done you’ll want to start thinking about how to contact anyone else that might be affected. While it’s important to act quickly to avoid any damage, it’s also important to be careful when contacting anyone affected so you don’t impact your relationship with them. If you’re team are involved at this point, Keep them up to date around what’s going on and be clear with them about any communication needs you might have.
While you wait for Xero support to confirm it was just the one invoice sent out and help you take back control of the hacked Office Admin account, you contact the customer that flagged the invoice with you to let them know things are in hand.
“Thanks for checking that invoice with us, we’ve got it under control now.
Have I told you how awesome you are recently?”
7 quick ways to improve the security of Xero in your business
This scenario is just one way a security incident in Xero could play out in your business. The bad guys are always looking for new ways to abuse services like Xero for their own purposes so it’s important to keep looking for things you can do to keep your business safe.
Here are 7 quick things you can do to improve the security of Xero today:
Start encouraging your customers, suppliers and team members to verify higher risk changes requested over email in person.
Check that user accounts in your Xero Organisation have Two-step authentication enabled.
Remind your team to use strong and unique passwords across every service they have access to.
Familiarise yourself with where to find logs in the Xero dashboard so you can quickly find them if needed.
Review the access each team member has in Xero and reduce (or remove) them where possible.
Check over the login reports for you Organisation as well as your own account for anything that looks dodgy.
Document the support details for Xero somewhere, ideally in an incident response plan.
More Xero security help
Our Cyber Fitness Platform can help you implement and keep track of these and other important security measures. Sign-up for free to see what’s involved.