Managing sensitive information in your small business
How confident are you that you know all the sensitive information lurking around in the recesses of your business?
How well is your team managing the personal information, health information, customer or contact details, tax file numbers and other data a privacy commissioner might care about?
If those 2 questions make your heart flutter a bit, you are not alone. Management of sensitive information in Australian small businesses is a tough job that most of us struggle with.
Data is not the new gold, data is the new uranium.
— Filippo Valsorda 💚🤍❤️ ✊ (@FiloSottile) August 16, 2019
Sometimes you can make money from it, but it can be radioactive, it's dangerous to store, has military uses, you generally don't want to concentrate it too much, and it's regulated.
Why keep uranium you don't need?
Data privacy has become a hot topic because the volume of data being collected on each of us has increased dramatically in recent years. It can be confronting to stop and think about all the systems collecting information on us, often without us even knowing about it. When information is stored by itself the harm is pretty minimal, but when collected and analysed in big data systems, it can become a goldmine for a cybercriminals and unethical competitors.
Over the last few months, you would have most likely done one or more of the following:
😷 Taken a medical pathology test.
🧁 Shared contact details to your local cafe for contact tracing.
💰 Completed an end of year review with one of your employees.
💸 Completed your end of financial year tax return.
📎 Shared a document containing confidential information with another business.
Each of these activities has you sharing or interacting with sensitive data you’ll want to keep out of the wrong hands! 👿
To your customers, clients, patients, donors, employees, suppliers and anyone else you work with there is a level of trust that you’re protecting the confidential information you hold. Any breach of this data will quickly lead to lost faith in you and likely drive them towards your competition. Once this happens, it will be difficult to recover your reputation and brand.
It can be tempting to think smaller businesses as interesting to cyber criminals as bigger fish like banks. Unfortunately, as the big fish 🐠 continue to improve the way they manage the security of their classified information, criminals are moving their attention towards the smaller, easier targets. 🐟🐟
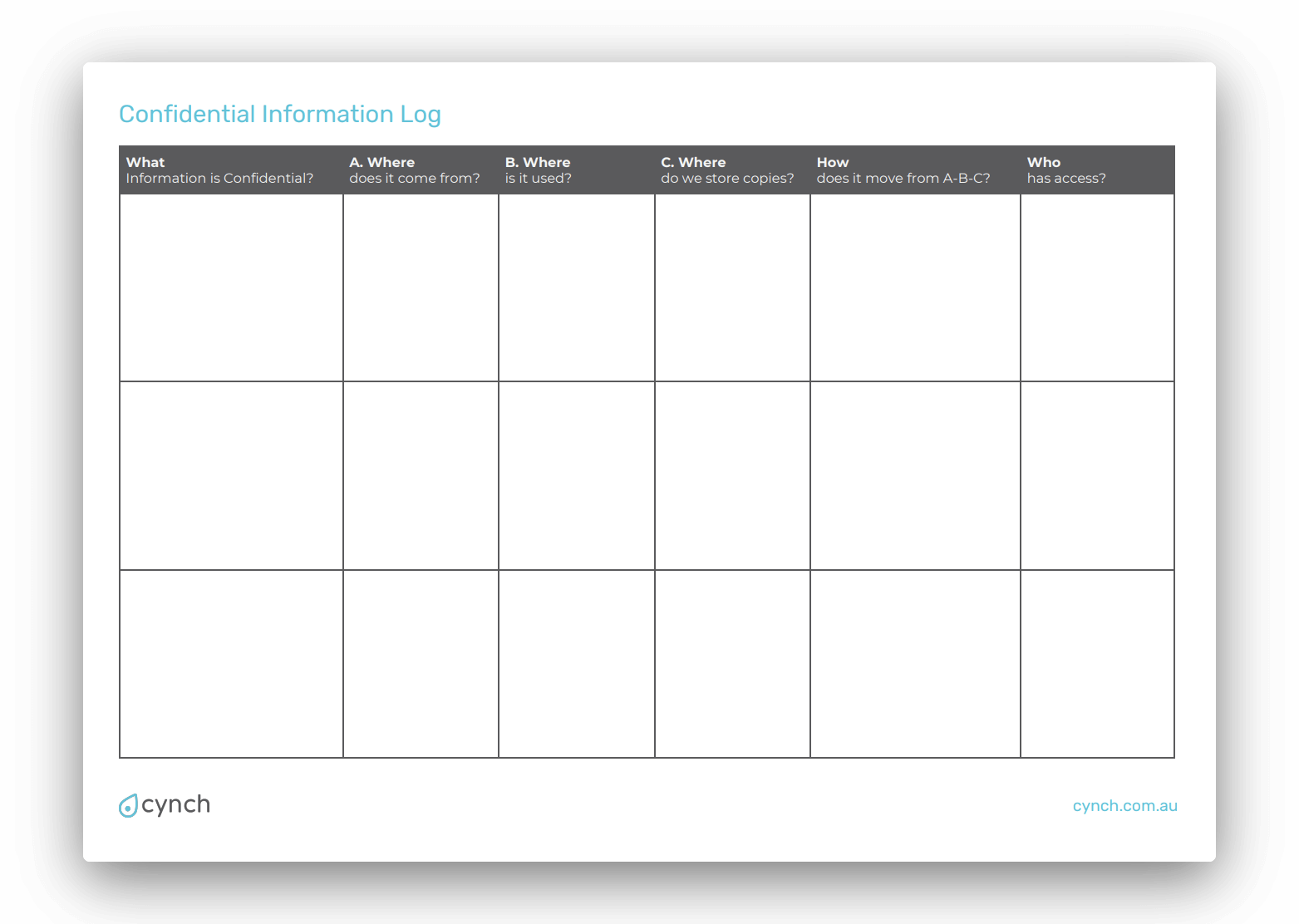
Before you start to worry about the privacy, protection and security of your confidential information, you need to understand the information you have, where it’s stored and who has access to it.
Download our free Confidential Business Information Log template to help you figure out what you should be prioritising.
Step 1. Figure out what information is sensitive
If you treated all the information you work with as sensitive, your business would quickly grind to a halt. Prioritising the protection of your ‘crown jewels’ is a good place to start. Ask yourself…
WHAT is the most important information in my business?
The answer to this question will be different for each business. It might be your customer contact details, patient records, or other personal information. If you don’t store personal information you might be more concerned about intellectual property or other confidential business secrets. If you have a team, your employee or financial information might be worth focusing on.
As a start, just choose one type of information and then rinse-repeat for others as required.
Step 2. Map out the data journey
Data is there to be analysed and used to gain insight and information. The journey of your data could see it move across a multitude of different places. Before going to far ask yourself…
WHERE is my sensitive information stored and moved?
Consider all the times someone interacts with the sensitive information you identified step 1.
Where does the information come from? From a website form, another system or your customer.
Where is it stored for being used? Eg. In a database, document, file share or in a filing cabinet.
Where is it stored for long term reference? Eg. back-up or archive copies.
How does it get from A to B and finally to C? E.g email, USB, cloud transfer or carrier pigeon 🐦
Step 3. Know who has access
Anyone accessing your data could potentially undermine any protections you put on it. When it comes to sensitive information, only those needing access to it for their job should have access. They should also know what they have access to is sensitive and understand what’s needed to ensure it stays protected. Ask yourself…
WHO can access your sensitive information?
Is it just those in your team, or can someone outside of your direct control (e.g. suppliers or customers) access it? Make sure you note down how someone would access your sensitive information as well to help you decide if certain data security measures will work for your business.
If at this point you identify individuals that have access to sensitive information that probably shouldn’t, consider removing their access wherever possible.
Case Study: Medical Pathology test results
Medical pathology tests have recently been fundamental for the safety of all Australians. Over 1.5 million tests have been performed across Australia for COVID-19 over the past 3 months.
Take a minute to contemplate the sheer logistics supporting this.
Someone takes the test
The patient contact details are captured
The sample is sent off to be analysed
Test results are recorded
The results are checked
Relevant medical service providers are notified
The patient is sent their results electronically.
Anonymous details are passed to another provider to aggregate in public statistics
And that’s just for a negative result!
For someone testing positive for COVID-19, more people will have access for contact tracing, treatment and whatever else is needed to help control the spread of Coronavirus. Privacy of this information is becomes even more important to avoid unnecessary alarm. 🚨
Step 1. Work out the stuff you need to protect
Pathology test results, patient contact details
Step 2. Map out the journey of your information
Where does the information come from? COVID-19 Testing Centre
Where is it stored for being used? Electronic copy and results in our Patient Management System, Hard copy in a filing cabinet.
Where is it stored for long term reference? In a cloud backup of the Patient management system.
How does it move between A, B and C? Sent from Testing Centre to the Dorevitch Pathology results system (medway portal) to our Practice Manager who enters it into our Patient Management system. The Patient then contacts our clinic to get the results.
Step 3. Know who can access your sensitive information
Pathology centres. Medical Practice Manager, Receptionist, Doctor, Referring doctor
For very detailed privacy advice specific to COVID-19 data, refer to the Office of Australian Information Commission website.
Once you have identified the sensitive information you need to focus on, you’ll be ready to start improving how it’s protected. We can help you quickly and easily complete these steps for your entire business in our Cynch Cyber Fitness Platform.