Secure access to your office technology during an emergency
In our previous post we discussed at a higher level seven cybersecurity considerations small businesses should keep in mind as they respond to Coronavirus. In this post, we’ll walk you through how to go about securing access to your office technologies.
We understand that all small businesses will be at different positions at the moment when it comes to the COVID-19 emergency. There's a lot to think about and work through, as this is the first time a global situation of this size has hit us. It is an emotionally and mentally draining time for us all.
Tens of millions of people around the world have suddenly found themselves under various forms of lockdown (CNN 17th March 2020).
At some point in the near future, Australians may also be asked to isolate ourselves at home. If this happens, it will change our way of living and working for a while, but businesses will need to continue. We know how critical small businesses are to the economy and want to make sure they can continue to work right through this crisis.
You may have already made the decision to work from home. You may have already decided that you will close temporarily. You may not have thought much about it at all yet, as there are just too many other pressing matters.
The trigger which leads to making this decision will vary from business to business.
Someone in your office has gotten sick, and you’re quickly forced to work from home in isolation;
You’ve decided as a company that you can move now, and have already done so;
You’re waiting for a government mandate (such as what’s happened in the US, Europe);
Those in your team with families need to stay home with their kids as schools are closing;
You’ve been wanting to move your workforce to be home based anyway, so this is good timing.
We’re doing what we can to help small businesses stay cyber fit during this stressful time.
Thank you to all those businesses out there helping to fight coronavirus! 💪
Work out what your technologies your business needs
We’ve created a simple exercise to help you identify the critical technologies your business relies on that may soon be stranded in your office. It takes only 5 minutes, which is less time than you might have spent ordering a coffee.
If you’ve never sat down and tried before, it can be tricky to figure out all the technologies you have running in your office. We help our members do this by capturing the technologies they encounter as we ask the following questions:
Take a look at what's on your desk
Look at what's on everyone else's desk
Consider what technologies you share with your colleagues
Think about where your any important files or documents might be physically in your office
Consider paper based processes that rely on printers
Think about how you find customer details and how you contact them
Think about how you get paid and how you pay your staff
Think about what technologies need to be checked if the power went out temporarily or permanently.
To help those businesses out there that trying to support their team as they put in place remote working arrangements, we’ve made this exercise available publicly. Cynch members (including free members) can also complete this exercise in our Cyber Fitness Platform to have the associated risks and recommendations automatically added to their account.
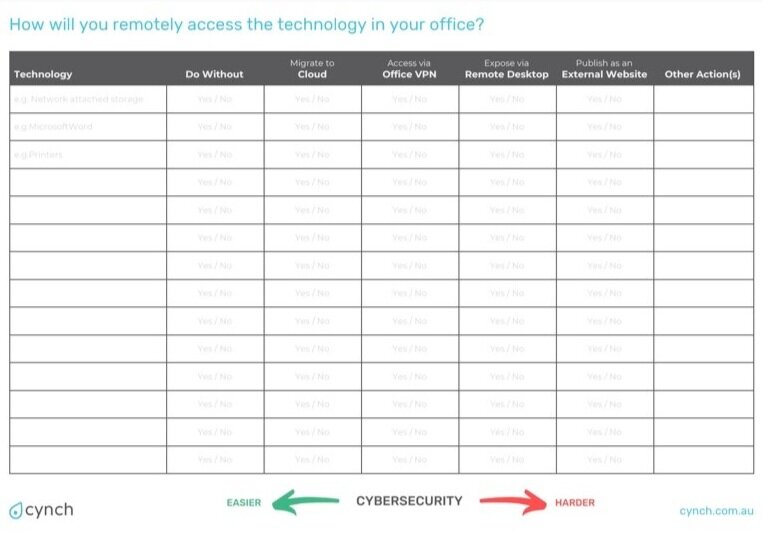
Spend a few minutes capturing the key technologies running in your office that your team might need to access remotely.
Some of you will walk away from this exercise realising that you have done more than you realised, others will better understand where they need to focus their efforts. To help we’ve also created a free workbook you can download to capture your choices around how the technologies you rely on will be made available remotely.
In the workbook, we list some remote access approaches that you may have heard about but may not understand. Don’t worry, you are not alone there. The table and flowchart in the next section will help you understand these technologies and the associated trade-offs so you can sound like a pro when talking with your IT support provider.
Understanding remote access approaches
Click to enlarge
The following table provides a brief summary of the various approaches you could take to making technologies located in your office available remotely. Once you’ve read the table you can use the flow chart to start making decisions around which approaches might work best for your business.
A couple of quick notes:
* We’re not endorsing these products but sharing them as examples in case you’re discussing them with your support provider.
** More information about these technologies and how to secure them can be found in the Cynch Cyber Fitness Platform.
| Remote access approach | Migrate to cloud | Access over Virtual Private Network (VPN) | Expose via Remote Desktop | Publish as an External Website | Do without |
|---|---|---|---|---|---|
| In a nutshell | Access your applications and documents from wherever, whenever and however. | It’s like a secret secure tunnel that allows you remote access to your office environment. | Allows you to work remotely on a computer or server physically located in your office | Allows external access to a web service/app or intranet. | Make a considered decision that you don’t need this technology |
| What's this useful for? | If you want to quickly set up and share documents within your team. | If you have a number of internal systems and custom built applications that you need to access remotely. | Accessing files on your work computer from home. If you have a role where you need to take control of a PC frequently. (eg. IT support) | If you don’t want to buy additional hardware and have a custom built web applications / intranet. To share information between businesses, clients, vendors etc. | If you decide that these are non-critical systems. You have found a workaround process / solution. |
| Some initial things to watch out for | Who can access the data? Default configuration. Access Controls. Document Management | Do they run the most current protocol? Data Limit, Will you be able to set up VPN access on multiple devices? How much will it cost? What’s best for the operating systems / types of devices you own | Lot’s of known and frequently attacked security issues. Setting up correctly is imperative to prevent compromise (See our platform). Can be complex depending on requirements. Bandwidth to your office. Make sure it’s patched | Time to set up. You will need to evaluate each application individually (Business Application Profile and User Application Profiles). Cost to set up, integrate and maintain securely. Liability Risks and 3rd party agreements | Decide early. It could be harder to migrate to a new technology if you physically cannot enter your office anymore. |
| Bonuses | Easy to set up and use immediately. All files are automatically backed-up. Document history kept. Accessible from any device | Auditing, Restrictions set on where and when staff can operate | You can continue to operate as you do today without the hassle of migrating to the cloud | No effort or money spent! | |
| Common Examples * | G Suite, AWS, Microsoft Office 365, Xero, MYOB, Square | Cisco Anyconnect, Fortigate, Red Piranha, UTM Devices | Microsoft RDS , Team Viewer, VNC, Vmware VDI | Custom web apps, Extranets | Printers |
| Security considerations ** | Implementing Access Control, Turning on Multi Factor authentication | Turning on Multi Factor Authentication | Turning on Multi Factor Authentication | Utilising a Firewall, Turning on Multi Factor Authentication, Implementing Granular Access Control, Enforcing Encryption |
Congratulations 👏👏👏
After a bit of brain gymnastics, you deserve to give yourself a pat on the back
At this point you should:
Understand what technologies you have in your office that you need to keep your business operational.
Understand the different types of remote-working technologies available to your business.
Have started to determine which approach you want to pursue for each technology and which technologies you can do without for awhile.
What’s next?
Now that you’ve identified the technologies you can’t operate your business without, our next post will talk you through how you can protect the information and equipment you have to leave behind.
🚨 Help is at hand!
We’ll be hosting a webinar to talk through keeping your small business cyber fit while working remotely during an emergency, where we will step through our top recommendations, share some anecdotes from businesses we’re helping and answer any questions you might have.
Sign up to our coronavirus notifications and we’ll let you know how to access the webinar.
“The world as we have created it is a process of our thinking. It cannot be changed without changing our thinking.”